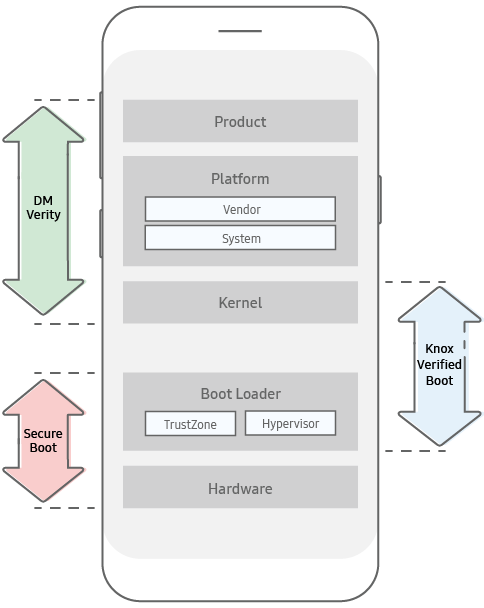
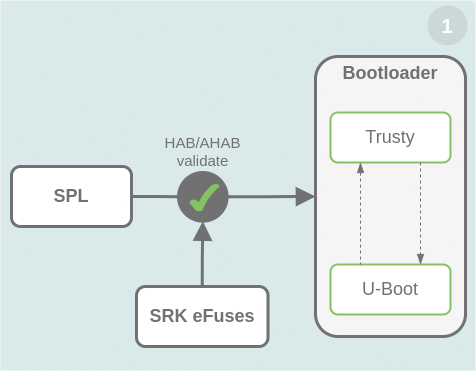
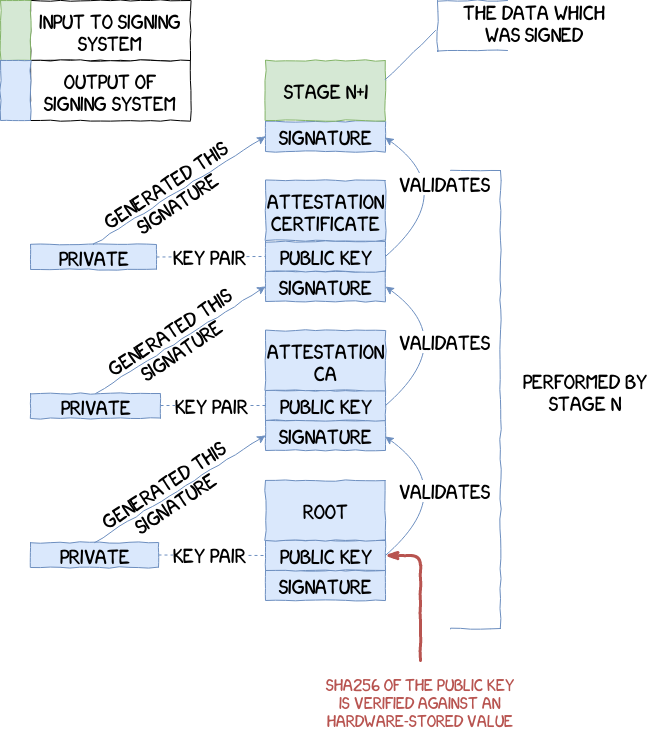
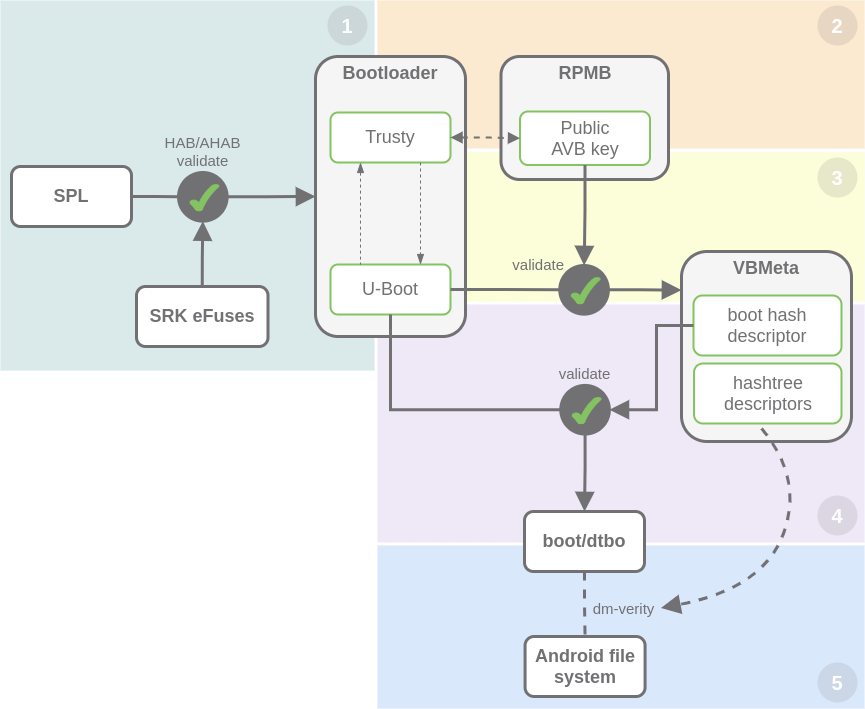
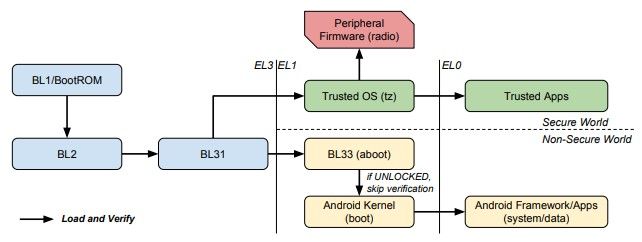
Forensics acquisition — Analysis and circumvention of samsung secure boot enforced common criteria mode - ScienceDirect

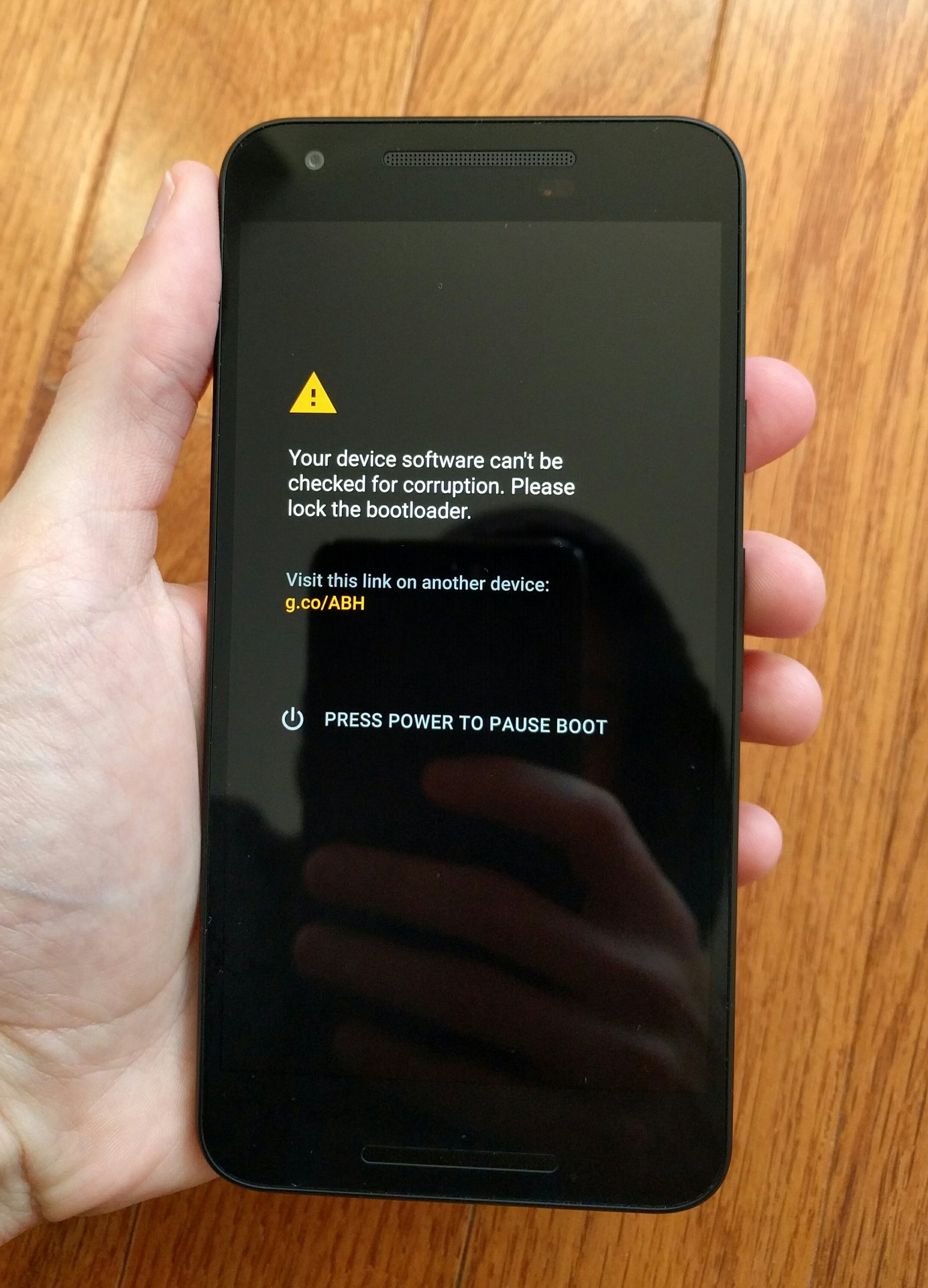
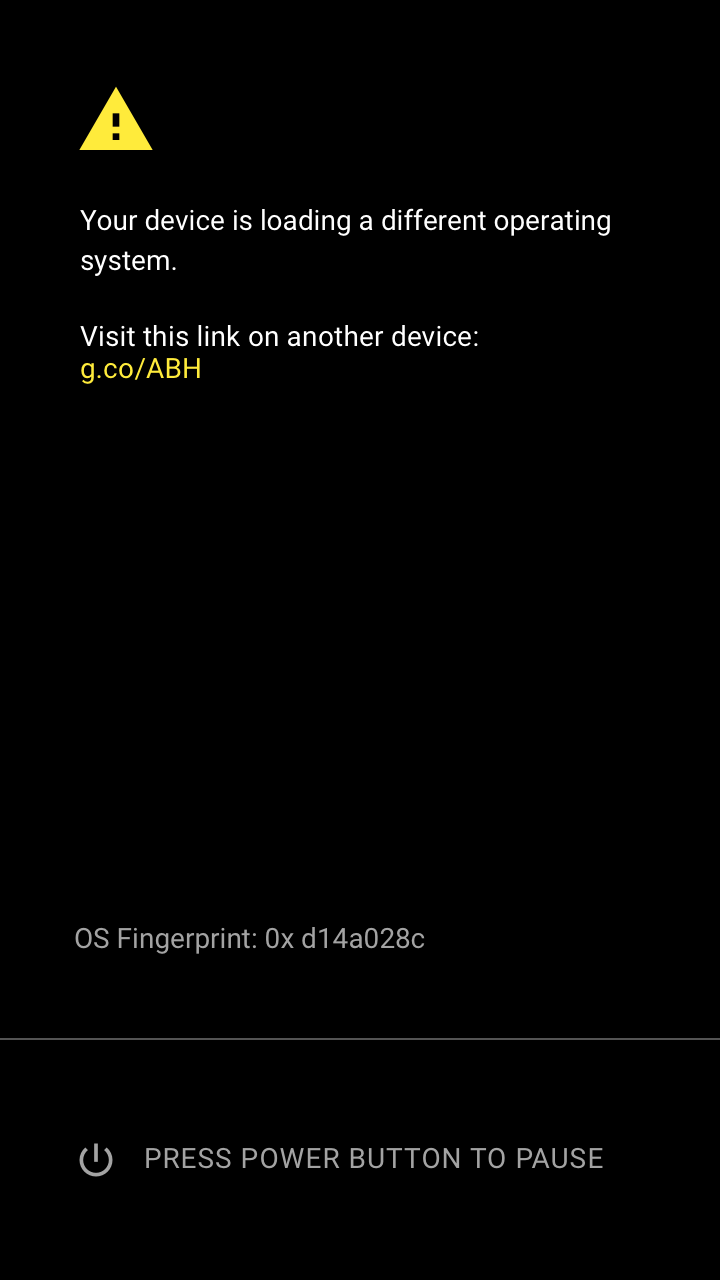
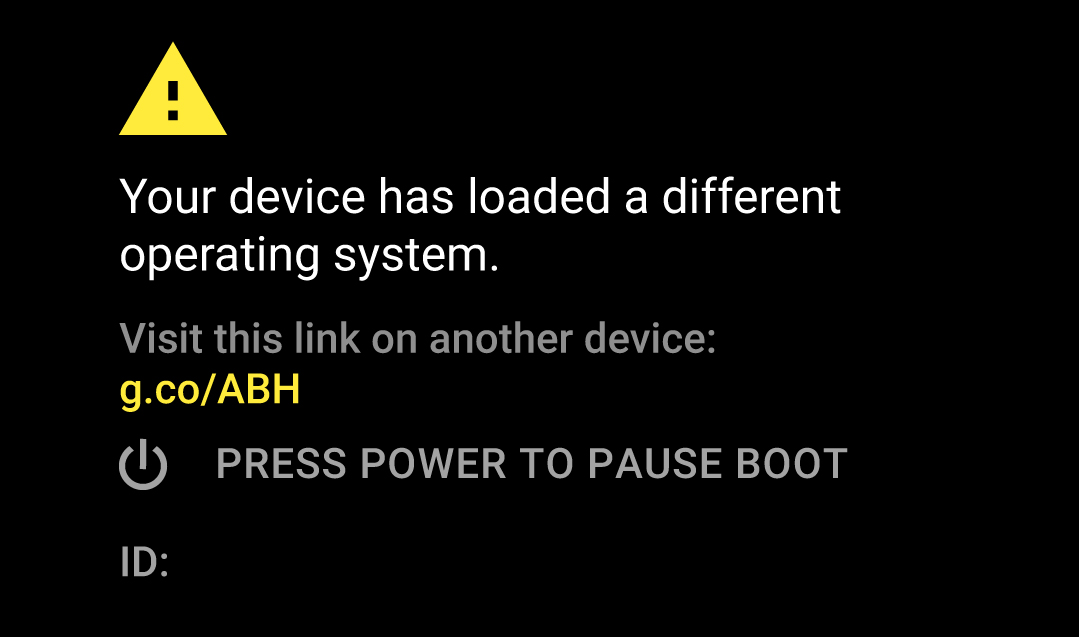
Android Oreo feature spotlight: Rollback Protection, a new part of Verified Boot, won't allow you to start a downgraded OS